
Some Redditors are celebrating the fact that “the front page of the Internet” isn’t changing by too much.
The post Reddit Racists Cheer News Their Subreddit Won’t Be Banned appeared first on WIRED.
Unrelated to the whiskey.

Some Redditors are celebrating the fact that “the front page of the Internet” isn’t changing by too much.
The post Reddit Racists Cheer News Their Subreddit Won’t Be Banned appeared first on WIRED.

If you ever go places or have things delivered at home, the Highway Trust Fund is critical and directly impacts your life.
The post Oh Good, We’re Out of Money to Fix Our Roads—Again appeared first on WIRED.
 Dubbed the “Netflix for Pirates,” the Popcorn Time app quickly gathered a user base of millions of people over the past year.
Dubbed the “Netflix for Pirates,” the Popcorn Time app quickly gathered a user base of millions of people over the past year.
Its popularity has also drawn the attention of copyright holders, who’ve made several attempts to shut the service down.
Today Popcorntime.io, the original and most used Popcorn Time fork, became the target of the latest takedown effort.
A few hours ago the domain name’s status was updated to “reserved,” which effectively means that the Internet Computer Bureau registry seized the domain name.
The UK-based registry previously took control of The Pirate Bay’s .ac domain name as well.
Popcorntime.io is “reserved”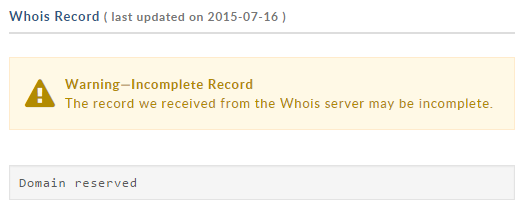
The domain name may still work for some if the DNS entries are cached, but it will soon be unavailable everywhere.
At first sight the Popcorn Time application itself appears to work just fine, most likely because it doesn’t use the .io domain for any crucial functions.
Popcorntime.io is not resolving
The server of the Popcorn time site is also unaffected. This means that people who enter the direct IP-address can still see the site’s homepage. However, none of the links work, including the download, as these all point to the .io domain.
TorrentFreak reached out to the Popcorn Time team for more information and we will update the article if we hear back.
The most likely scenario is that the Popcorn Time team will switch over to a new domain name. They already own popcorntime.re and popcorntime.cc but at the time of writing both point to the seized domain.
Developing story, updates may follow.
Source: TorrentFreak, for the latest info on copyright, file-sharing, torrent sites and the best VPN services.
Source: TorrentFreak
 As the increasingly epic legal battle over every aspect of Kim Dotcom’s copyright infringement case continues, the latest focus has fallen on computers and other devices previously seized from the entrepreneur.
As the increasingly epic legal battle over every aspect of Kim Dotcom’s copyright infringement case continues, the latest focus has fallen on computers and other devices previously seized from the entrepreneur.
While some encrypted data has already been sent to the United States, the content is inaccessible due to U.S. authorities not having access to the passwords. Other data, cloned in 2013, is currently in the hands of New Zealand authorities.
This data is also of interest to the United States government as it builds its case against Dotcom and his associates. Earlier this month the New Zealand Attorney-General’s appeal to quash restrictions around sending the seized devices to the U.S. continued, with the Crown arguing for the clones and their passwords to be sent to the United States.
Partial objection to the move came from Kim Dotcom’s lawyer Ron Mansfield. While filing no opposition to the majority of the 2013 cloned data being sent to the U.S., Mansfield said that agreement could only be reached if the data was stripped of personal information and other data irrelevant to the United States’ case.
That suggestion was rejected by the Crown as impractical, with a note that even if such a task could be undertaken, New Zealand authorities would not be able to recover the costs of doing so from the United States. Mansfield’s opposition to the release of the passwords relating to the 2012 data was also opposed.
This morning three Court of Appeal judges handed down their decision and it represents a setback for Kim Dotcom and associates Finn Batato, Mathias Ortmann and Bram van der Kolk.
In their ruling Justices Douglas White, Tony Randerson and Lynton Stevens set aside earlier High Court rulings, which now frees the Attorney-general to issue new directives to police under the Mutual Assistance in Criminal Matters Act. This will enable the cloned devices to be sent to the United States.
However, it will come as little surprise that the decision is open to appeal. According to the New Zealand Herald, Dotcom and his associates will be able to challenge the move in a new judicial review in the High Court if they so choose.
With another ruling behind them, attentions now turn to Dotcom’s extradition hearing. After several delays the hearing is currently scheduled for September, but that date is also being appealed by the entrepreneur.
Source: TorrentFreak, for the latest info on copyright, file-sharing, torrent sites and the best VPN services.
Source: TorrentFreak

Netflix has recently expanded into offering Spanish-language shows on Netflix in the US. And the company says American subscribers are loving it.
The post US Subscribers Love Netflix’s New Spanish-Language Shows appeared first on WIRED.

Netflix announced its quarterly earnings today. And the company is doing great, thanks in large part to its popular originals.
The post Netflix Says Its Original Shows Bring In More Subscribers appeared first on WIRED.

The International Atomic Energy Agency (IAEA) has a lot of work ahead of it. Which means it needs the best people on the job. Which means (duh) including women.
The post Whoa, Someone’s Trying to Attract Women to Nuclear Science appeared first on WIRED.

The 2.7 RS is considered one of the purest Porsche race and road cars ever made.
The post The 1973 Porsche You Really Should’ve Bought 10 Years Ago appeared first on WIRED.

Many disgruntled shoppers are eager to share their opinions about Amazon’s Prime Day.
The post Shoppers Frustrated Over Amazon Prime Day appeared first on WIRED.
 Last month researcher Zammis Clark (known online as ‘Slipstream’) discovered a security flaw in Impero Education Pro (IEP), a not insignificant find given the software’s application.
Last month researcher Zammis Clark (known online as ‘Slipstream’) discovered a security flaw in Impero Education Pro (IEP), a not insignificant find given the software’s application.
IEP is widely used in UK schools to monitor and restrict students’ Internet activities. According to Slipstream, the flaw had the potential to expose the personal details of thousands of users’ to hackers.
Early last month the researcher announced his find on Twitter while noting that it would allow for remote code execution on all Windows clients. Within the tweet he posted a link to his proof-of-concept code.

“[Impero] had a booth at BETT back in January. They gave out donuts. Those were nice,” Slipstream wrote
“Unfortunately, when I asked about their security, nobody answered me. Some reversing later, looks like Impero is completely pwned amirite.”
While Slipstream ultimately advised against using Impero’s product, he says he didn’t immediately inform the company of the vulnerability.
“Not being a customer, I wouldn’t have known where to send it, or whether they’d even reply to me,” the researcher told TF. “And, given the severity of the issue, I figured that full disclosure would cause some sort of fix pretty quickly.”
In fact, that prediction proved correct, with Impero issuing a temporary security patch to fix the flaw.
“We immediately released a hot fix, as a short-term measure, to address the issue and since then we have been working closely with our customers and penetration testers to develop a solid long-term solution,” the company said.
“All schools will have the new version, including the long-term fix, installed in time for the new school term.”
However, Slipstream claims the patch wasn’t effective.
“Of course, their fix turned out to be inadequate. After speaking to Impero users on a forum who advised me to email Impero support, I did just that, responsibly disclosing to them exactly how their fix was inadequate and that I had an updated PoC that worked against it,” he told us.
At this point it appears that relations between Slipstream and Impero had already taken a turn for the worse. After disclosing the issues with the patch almost a week ago, this week he received a legal threat from the company.
“In breach of the license terms, you have modified the software without our client’s authority, you have decompiled the software for purposes otherwise than to achieve interoperability and you have published confidential information about our client’s software,” Impero’s legal team state.
“By publicising the encryption key on the internet and on social media and other confidential information, you have enabled anyone to breach the security of our client’s software program and write destructive files to disrupt numerous software systems throughout the UK.”

Impero’s lawyers say that Slipstream’s actions have caused “direct loss and damage” in addition to “reputational damage” and “potential damage” to numerous IT systems used by schools throughout the UK.
“The loss and damage to our clients caused by your activities is significant and will in any legal action taken in the civil courts be the subject of applications to the court for restraining orders to restrict you from further copyright infringement and breach of confidence as well as court orders for monetary compensation,” the letter adds.
After advising Slipstream to seek legal advice and setting a deadline of July 17, Impero’s lawyers suggest that the damage to their clients could be mitigated if the Github posting and all associated Tweets are taken down. That has not yet happened.
Slipstream is disappointed by the threats and informs TF that taking action against researchers like himself could even prove counter-productive.
“Legal threats here would just be ‘shooting the messenger’ so to speak, and would discourage security researchers from actively reporting any issues,” he explains.
“Such legal threats to security researchers would certainly not prevent any malicious individuals from finding issues themselves, and using them for malicious purposes.”
Indeed, this last point is particularly relevant. Slipstream says that he knows someone who has found two other security issues in Impero’s software. Whether they will be tempted to speak to the company considering its aggressive legal response will remain to be seen.
Source: TorrentFreak, for the latest info on copyright, file-sharing, torrent sites and the best VPN services.
Source: TorrentFreak